Personal Firewalls
Kerio Personal Firewall
Introduction
Kerio is Tiny Personal Firewall under a different name. Guess it was sold and/or branched. A more powerful alternative to the basic version ZoneAlarm. Unlike ZA, Kerio works on a gateway to protect a LAN connected to the Net... but experience shows that it is not heavy duty in this role; So don't be surprised if you experience occasional problems if using Kerio in this role.
Also, since open NetBios ports is a classic mistake, Kerio comes with a specific configuration tab to close those ports from the Net (although some users say that it's not reliable, and prefer to not use this, and build their own rules instead.)
Generally speaking, the rules that Kerio build for you automatically if you let it are (to quote a users) "weak and flawed. The default rules that come with the firewall are worthless, and will not protect anyone from the Internet. Going one step furter, the old stand-by rules passed down from AtGuard days and rewitten for for Tiny, are woefully out-of-date and have holes large enough for a truck-load of exploits to drive through." You've been warned :-)
Setup
- Dowload and install from the vendor's site
- Reboot, even if running W2K
- Get rid of all the default rules, as most of them can be agregated into a few, general rules
- If this host is acting as a gateway, test from both this host and other hosts on the LAN
Here's a basic configuration, for a single host (ie. not acting as a gateway) connected in ADSL:
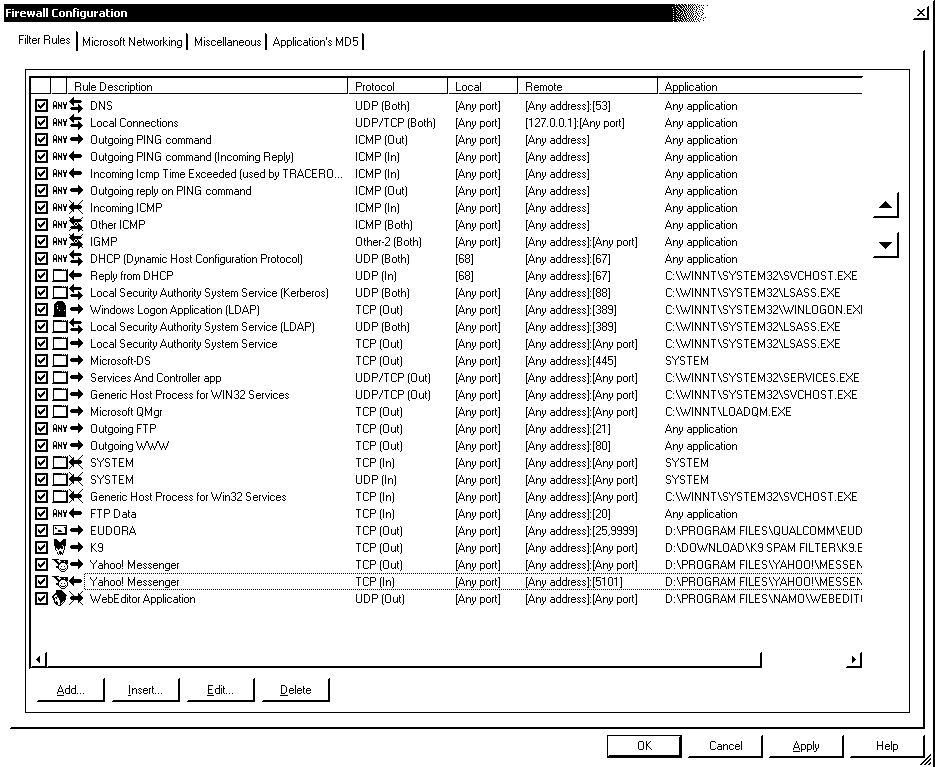
Remarques:
- Note that if you are connected using a cable-modem, I read that this kind of ISP pings hosts to check if it is still alive. I assume that banning those incoming pings means that after a while you while disconnected.
- Eudora connects to the K9 anti-spam proxy for POP3, but needs to connect to an SMTP server at the ISP to send e-mail.
- I changed the default settings for Yahoo for reasons explained at the end of this document
- I made use of the Microsoft Networking tab instead of writing my own rules to protect use of NetBios
- If you add a final "Block All" incoming/outgoing rule for all protocols... Kerio will no longer prompt you when a new application wants to go through
Here's one for a W2K using ICS to act as a gateway to the Internet:
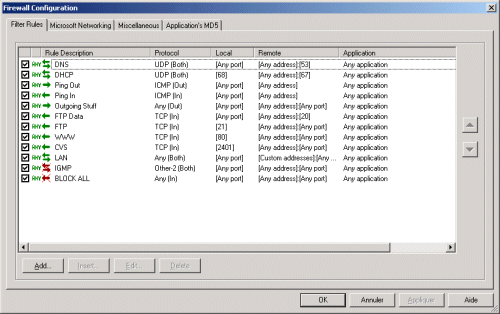
As you can see, you need to allow other hosts on the LAN to go through this host on their way to the Net. Checking "Is running on Internet Gateway" is not enough. Remember to add the LAN network address in the Custom Address Group in the Miscellaneous tab.
As added protection, I added a catch-all DENY ALL rule. Since rules are applied top to bottom, this rule has to be the last in your list. This catch-all rule with make the gateway stealth.
To let users work with an FTP server on the Net using the default active mode, add a rule to allow incoming TCP packets from any server, source port 20.
Important: If you are connected through a cable-modem, it is possible that your ISP pings your host regularly to see if it's still alive. In this case, write a rule to let incoming PINGs from your ISP, or you will experience mysterious disconnections after a certain amount of time.
Some users have reported that Kerio doesn't support gateways as well as eg. Sygate, since it's originally meant to run on a stand alone host.
Configuration
According to the different Kerio forums I checked, the default filtering rules provided by Kerio are not good. Hence your having to dive into this right from the beginning.
First of all, some users prefer to not use the Microsoft Networking tab, and build their own rules to protect their LAN from attacks aimed at the NetBios stuff.
Also, to protect against spyware, ie. legit software that connects out to the Net without telling you and for no reason (eg. why would an HTML editor like Namo WebEditor connect to the mothership without asking my permission? ;-)), some users prefer to write rules to specifically allow such and such application to connect out, and forbid all others.
I recommend you start with a basic and working configuration which allows any outgoing connects (thanks to Kerio being stateful, responses are handled automagically), and, if you are running some service such as a WWW server on this gateway that must be reachable from the Net, allow those specific incoming connections, while banning all other flows.
Windows EXEs
- SERVICES (Services and controller app)
- SVCHOST (Generic host process for Win32 services; Process used by Windows NT platforms to allow services to run and link with other applications; Should NOT be denied access NOR disabled; DNS Client, Windows Time, RPC/NetBIOS and other services use the svchost.exe; Actually the svchost.exe is an "application" that enters multiple process states from the system (Windows) to perform system serviced tasks as an application. It can be safely denied Network access but it is impossible to "disable" (it's not allowed by Windows) because of its system service dependencies for Windows to function. Also if you attempt to end some of it's critical processes (which isallowed) you will crash Windows. :)) It is true that the svchost.exe does access the Network/Internet and no, there are no problems with this if you have legitimate services that you require. The problem is that the operating system (Windows) manages this application and because the svchost.exe serves "multiple purposes", it can be a trusted path for any registered service (deemed so by Windows) that you may not want having network access. At that point the firewall can only control this application by way of Internet Protocol if it is already a trusted application. Funny, under Win2k I have DNS and DHCP handled by services.exe, not svchost.exe. RPC/NetBIOS is handled by svchost.exe, but those I would not want to be accessible over the Internet. I've never used W2K, there must be a slight difference with the loaded services because XP uses the svchost.exe for most of the network service based functions. I rarely have seen XP use the services.exe for any TCP/IP outside of my LAN with my current set up, but I imagine it could for any service if needed. The service.exe is described as a "services and controller" application process, probably leaving most of the footwork up to the svchost.exe as a host. At present for me the only registered services in the service.exe process is Event Log and Plug n Play. Since W2K and XP are within the confines of the NT family, the differences are probably minimal in most respects. The administrators set up and/or the operating systems designation plays a role of some kind.)
- LSASS (Local Security Authority System Service): LSASS is the Local
Security Authority Subsystem. It receives authentication requests from Winlogon
and calls the appropriate authentication package. There have been reported
numerous exploits and DoS scenarios for LSASS, so I strongly disrecommend
having LSASS open to communicate with the Internet. There is a particular
exploit using null sessions, leading to filled-up session arrays in LSASS.
The worm Lovgate will also abuse LSASS. If LSASS crashes, your system willeither
reboot automatically or simply deny any further logon attempts for you.
In typical home use scenarios, but also in most corporate environments, LSASS does not need any network privileges beyond loopback traffic, so I keep that door closed in my firewall rules. In the worst case, you will have to enable LSASS to access the local network to talk to some authentication server (Win2k or WinXP), but NEVER enable that for the Internet connection. - WINLOGON (logon through LDAP)
- MSTASK (Task scheduler engine)
- SYSTEM (in C:\WINNT?)
- MS-DS (Directory service?)
- RUNDLL32 (Run a DLL as an app)
- MOBSYNC
- LOADQM (Queue manager)
- MSHTA
- MSIPCSV (IPC Server)
Windows Ports
- TCP 135
- UDP 135
- UDP 137: Netbios Name Service. You may need it on your local network but it should definitely be disabled over the Internet
- UDP 138
- TCP 139
- TCP 445
- TCP 593
Troubleshooting
- As with any firewall, order matters, eg. if the first rule denies any connection, you can have all the permit rules below, it won't work. Use the up and down arrows on the right side of the Filter Rules dialog
- You can set up a group of Custom Address Group (Miscellaneous tab in the Administration | Firewall Configuration dialog)
- If this firewall is running on a host acting as gateway, make sure you check "Is running on Internet Gateway" in the same dialog to ease configuration
- Not sure what the difference is between one-way and bidirectional flows. Since Kerio is stateful, why should we have to choose bidirectional at all? UDP?
- When making any change to the list of rules, make sure you click on Apply/OK, and close/reopen. Otherwise, changes are not displayed (but are be activated once you clicked on Appy)
Q&A
What does "UsrRsltMd5AddApp: You have too many application already registered!!" mean?
Too many files listed in the MD5 program listing within Admin. Delete duplicates and old programs, save, and restart.
How to go back to default rules?
persfw.conf is your current ruleset. I believe that if you stop the firewall and rename that file, you'd be back at the default rules. Kerio should remake the original persfw.conf file with the original rules when the firewall is restarted. Deleting or renaming the file makes no difference other than that if something went wrong, you could change the name back if you only renamed it.
Stat.conf contains your settings for Kerio's status window.
What does Both Directions mean?
Since Kerio is a stateful firewall, why would I need those?
By default, Kerio allows Microsoft-DS/SYSTEM to connect out to TCP 445. Shoud I keep this rule?
No, it is unneeded and will cause you a tremendous amount of grief. You should be able to remove this rule. It certainly shouldn't be allowed TCP access. Ugh!
Why do I have to allow "Generic Host Process for Win32 Services" to let a private host access a web server on the Net?
Resources
Tiny Personal Firewall
http://www.tinysoftware.com/home/tiny
Here's a working set of filtering rules for TPF 2.0.15A on a W2K Pro host running as an Internet gateway
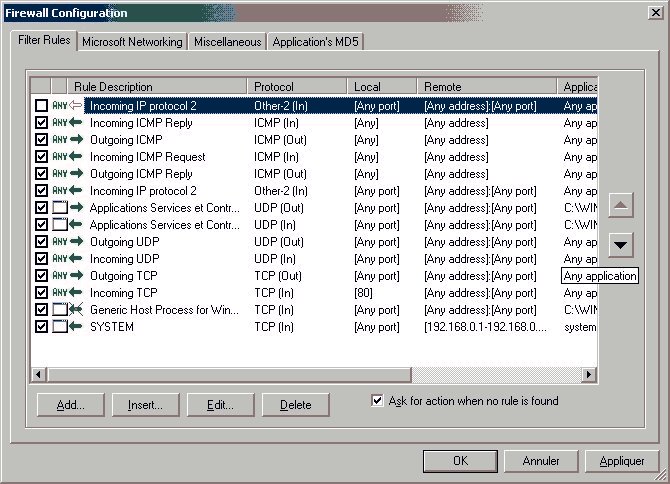
As of now, I have no idea what IP Protocol 2 (I unchecked it), and I doubt this is a secure configuation (eg. allow incoming UDP datagrams from any host...).
Outpost
Look'n Stop
ZoneAlarm
The basic, free version doesn't offer as much control as Kerio (eg. allowing/denying based on remote IP or port), and doesn't work on a gateway host.
??? "If you are using ZoneAlarm on the gateway computer of a shared Internet connection, check that the computers in your local network have been added to your Trusted Zone. If you do decide anyway to use free ZoneAlarm on the ICS gateway machine, Internet Zone must be set to Medium setting (ZoneAlarm on the ICS client machines can have Internet Zone set to High). Note that if the Internet Zone is set to medium, the PC will not be stealthed, so this is not recommended.
On some systems, Generic Host Process (GHP) or SERVICES.EXE may ask for server rights to connect to DNS; if so, add your DNS servers to your Trusted zone only; then give server rights to GHP and SERVICES.EXE for the Trusted zone only. In addition, ZoneAlarm does not have automatic network configuration, so the ICS network must be added to the Trusted Zone manually."????
BlackICE
Sygate
http://www.sygate.com/free/spf_download.htm
Deerfield personal Firewall
http://www.deerfield.com/products/personal_firewall/index.htm (free 30 day trial)
Norton Personal Firewall
http://www.symantec.com/sabu/nis/npf/
Q&A
Should I allow any outgoing traffic?
Trojans and worms do their damage by using your system as a "launching pad" for their payloads. Outbound traffic monitoring is as important as inbound traffic monitoring. It's up to you whether you want to spend time configuring your host when installing a firewall, and update it every time you add an application that needs to connect out.
Which anti-virus software should I use?
Many users recommended AntiVir Guard, AVG, Avast, and NAI's Stinger.
Why do I have trouble using FTP?
FTP comes in two flavours - Active and Passive. Most ftp clients (including WSFTP) are active unless explicitly told to be passive.
With Active FTP, the process looks like this.
- FTP Client Connects into FTP server on port 21: (Random port) ---> (Server:21)
- FTP Client logs into FTP server using the connection
- FTP Client requests Directory listing and gives a random *local* port as a target)
- FTP Server connects to specified port from port 20 (New Random port) <--- (Server:20)
- FTP server sends directory listing across connection opened in (4)
With Passive FTP, the process looks like this:
- FTP Client Connects into FTP server on port 21: (Random port) ---> (Server:21)
- FTP Client logs into FTP server using the connection
- FTP Client requests Directory listing and specifies Passive)
- FTP Server Sends random port number back along connection already opened
- FTP Client connects to FTP server on the port specified by the server (New Random port) ---> (Server:Random port)
- FTP server sends directory listing across connection opened in (5)
Now working from there - if you are using Active mode, you *must* have a rule that allows the ftp server to connect back to you. otherwise, you must set your ftp client to Passive mode *and* allow your client to connect to any port on the server.
You only have three options:
- Only use passive FTP and permit the ftp program to connect out to any TCP port on any remote address.
- Trust your FTP program and permit any incoming or outgoing TCP traffic for this program.
- Enable outgoing TCP connections from any local port to any remote port for that program (port 21 for active FTP, all others for passive FTP), plus incoming connections from tcp port 20.
In any case, the second approach should work. If it does not, there is something else in your configuration that shouldn't be there.
Why is the MTA running on my gateway slow to send out e-mail?
One likely possibility is an Identd check on Port 113, some FTP or e-mail servers check Port 113 though most of these normally still work but are very slow. Try a rule Allow, IN, Local Port 113, Remote IP - (IP of server), Remote Port - any.
Application-specific information
Rules for loopback
From a pragmatic standpoint, I would recommend having a permit-all rule on loopback, i.e., 127.0.0.1 to 127.0.0.1 for ICMP, UDP and TCP traffic... In fact, I have such a rule. :-) However, I do not run any specific services on loopback. They're all bound to the local IP address of my Ethernet interface (which happens to be 10.x.x.x at home and a class B address at work). That's a local SMTP server, POP3 service, HTTP, FTP, SOCKS4 proxies...
Blocking port 135-139, 445
Since those are the best candidates for intrusion, create a rule near the top of your rules: Rule 2 (DENY external access) UDP (In) Remote port: Any Remote Address: Any Local ports: 135-139,445 (ports used by Windows Messenger).
To block port 135 specifically, you can also do it via the registry (set "N" for the HKEY_LOCAL_MACHINE\Software\Microsoft\OLE registry key "EnableDCOM" named value) as per MS Knowledge Base Article 158508.
Yahoo Messenger
By default, once you're chatting with someone, an incoming connection is made from this remote host. To avoir having to open a port each time (and since most people use dynamic IPs, it changes each time), change the Connection settings to "Firewall with no proxies"
Internet Explorer
When you launch IE and run Kerio's Status applet, you will see that IE listens on a UDP port (1459.) Basically Internet Explorer is attempting to look at the temporary files cache to determine if the page is currently in memory (in which case it does not need to be downloaded again,) of if it is new and needs to be downloaded. IE will function without access, but will wait for a timeout to continue.
You would be far better off in creating a UDP loopback rule to allow*all programs* to access the loopback address. As this address is located within the machine, and does not go out to the Internet, there is no danger in allowing all programs to use it. (There areseveral other programs besides IE that use a loopback for various functions.)
Always remember however, that UDP should never be allowed in or out through the firewall, unless you know the specific programs & address that those programs are accessing. UDP is connectionless and can be used to ebstablish an unauthorized connection by an outside party. Basically I would recommend you set up UDP rules (ONLY) for DHCP (if your ISP uses this, probably don't need it if you are using PPP) & DNS. Then the basic loopback (discssed above) and that's all! Allowing ANY other access for UDP can open a can of worms.
Resources
Documentation
- http://grc.com/port_0.htm . Replace the digit with the port in which you are interested
Utilities
Scanning your host
- Symantec Security Check
- BlackCode
- DSLReports
- AuditMyPC
- Steve Gibson's Shields Up (Only tests TCP ports. You might find a more thorough port scan at speedguide.net)
- PortDetective (requires installing an application on the host you wish to test)
- Sygate